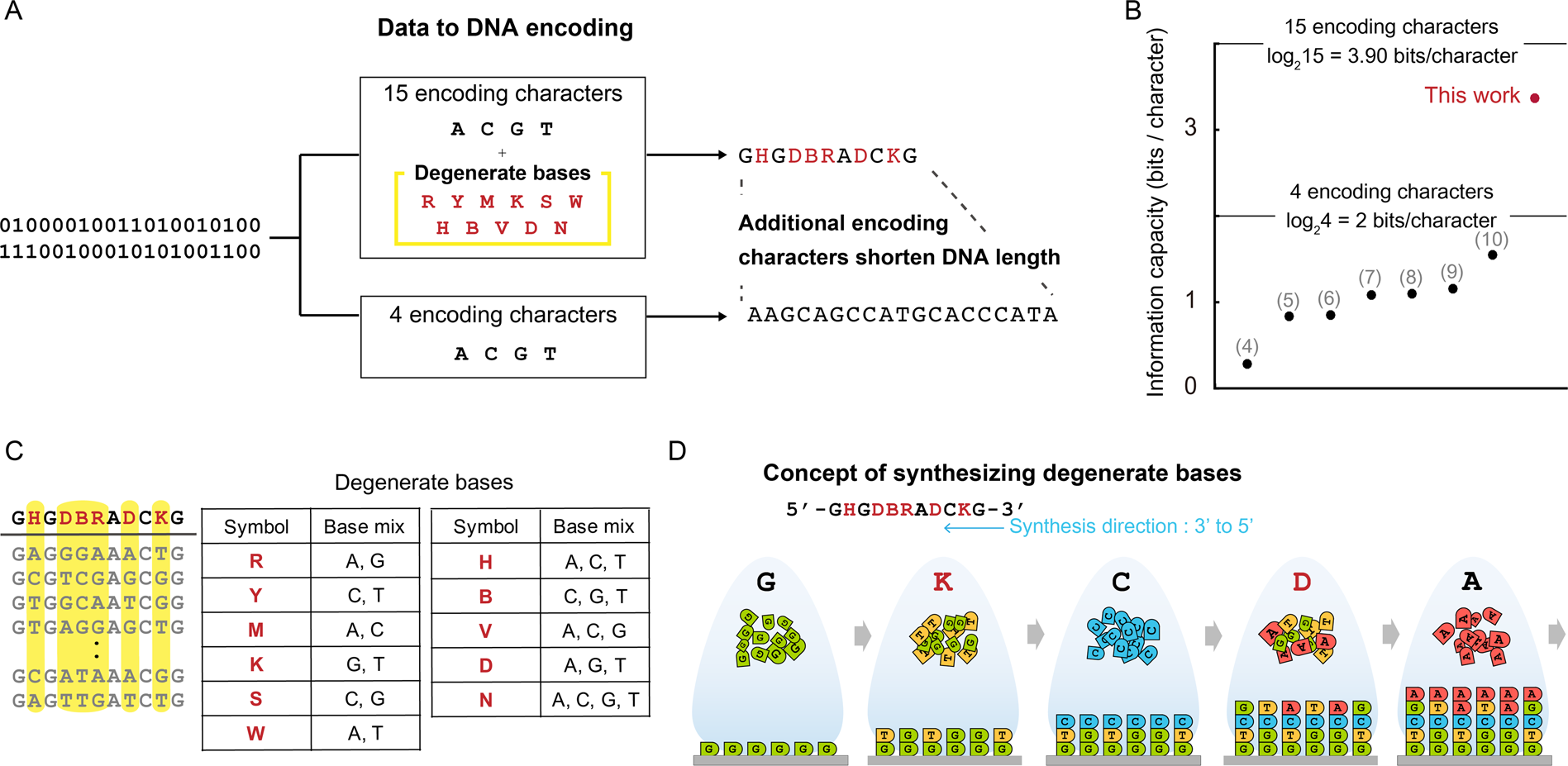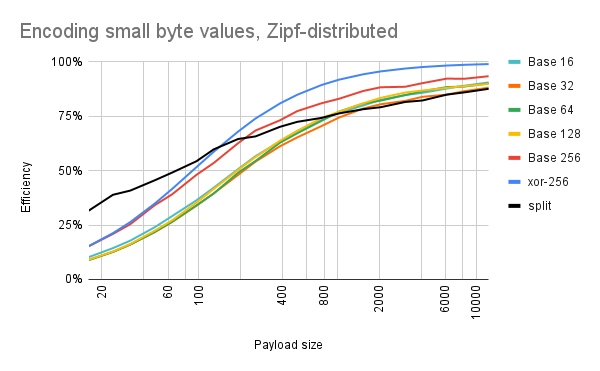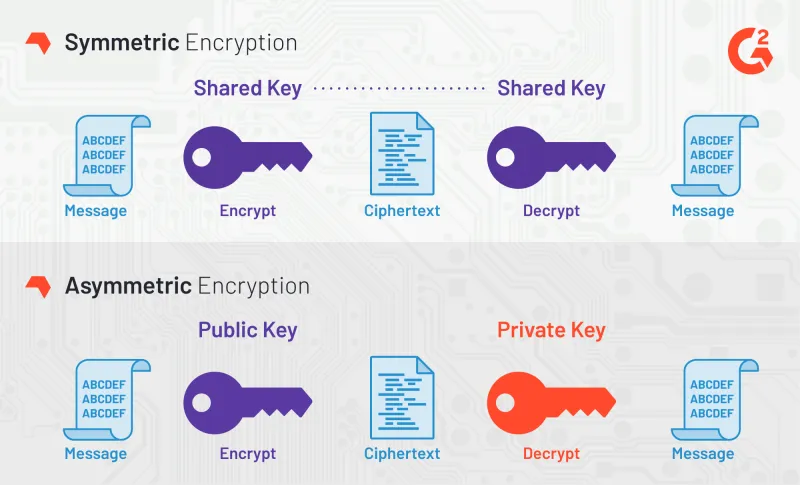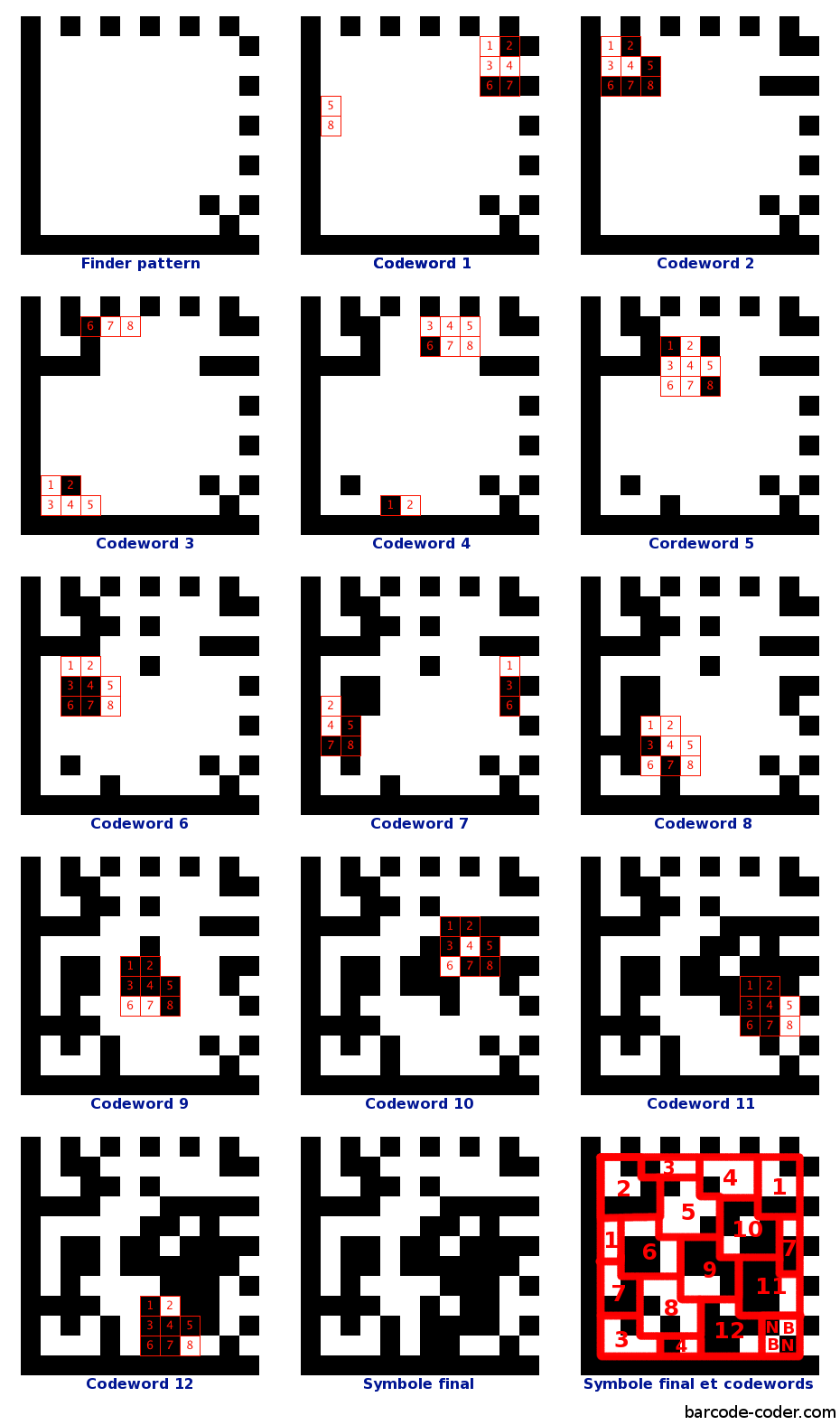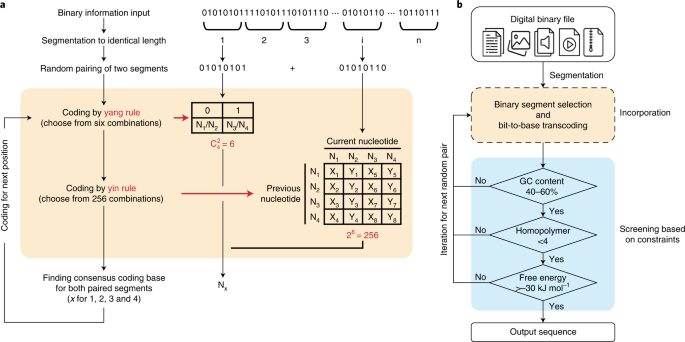
Towards practical and robust DNA-based data archiving using the yin–yang codec system | Nature Computational Science
GitHub - fabiospampinato/base256-encoding: Base256 encoding, the most memory-efficient encoding possible in JavaScript.
GitHub - fleschutz/base256unicode: Simple C++ sample program to represent binary data in base 256 encoding using Unicode.
Entropy | Free Full-Text | A New Algorithm for Medical Color Images Encryption Using Chaotic Systems

4300g does not use all the cpu power when encoding. 4500u uses more cpu with the same instructions. : r/Amd

elementary number theory - How Does This Base Conversion Algorithm Work Exactly? - Mathematics Stack Exchange